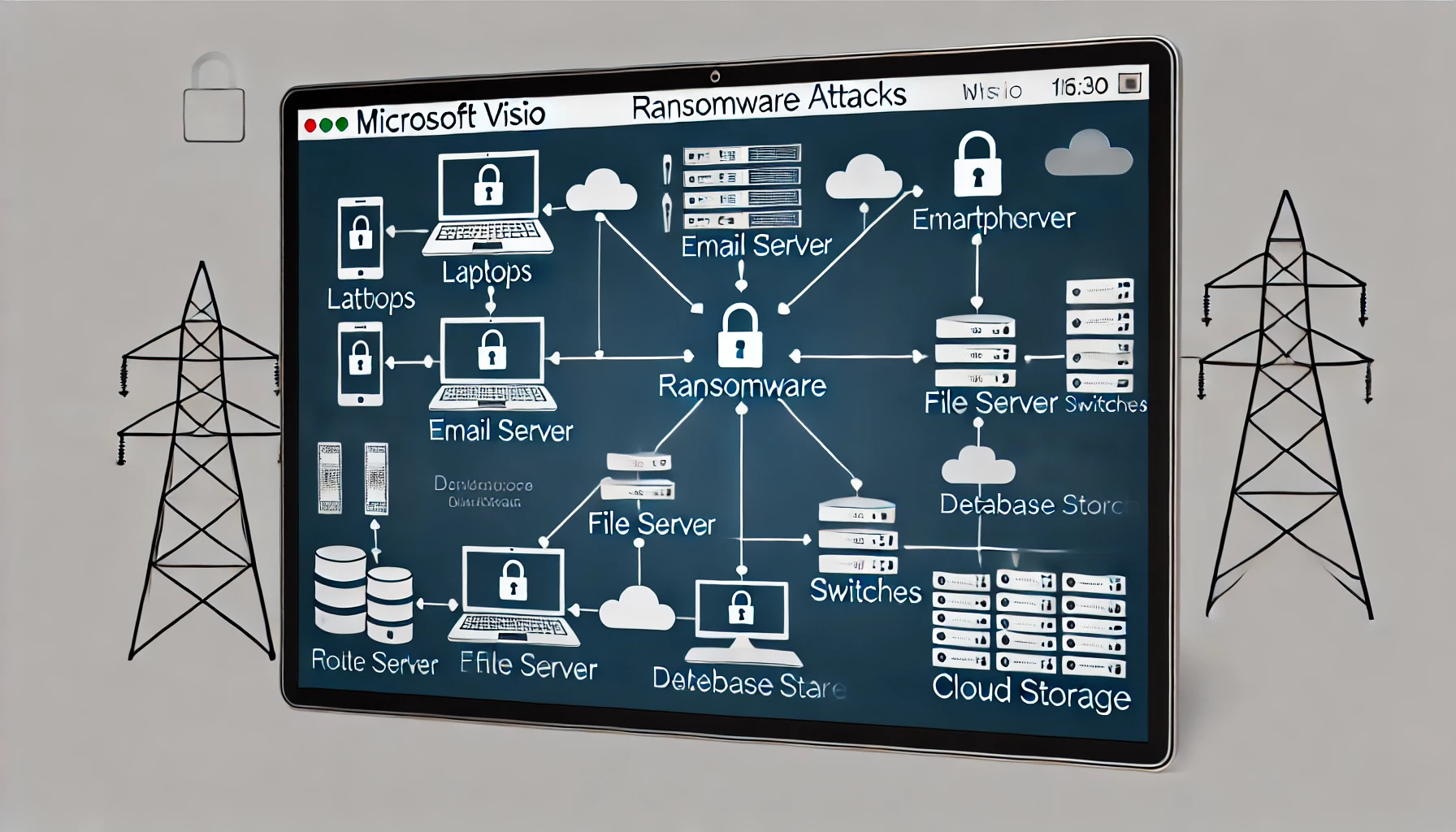
Diagrams illustrating ransomware attack vulnerability points within a computer network can be highly beneficial in understanding and enhancing network security.
The following are nodes in a computer network that often become targets for ransomware:
- End-User Devices: Laptops, desktops, and mobile devices used by employees. This is a primary entry point because they are often connected to the internet and access emails or websites that could potentially contain malware.
- Email Servers: Servers that manage emails for an organization. Phishing attacks via email are often used as a method to spread ransomware.
- File Servers: Locations for storing files and data. Because they often contain important data, these servers are prime targets for ransomware attacks.
- Network Devices: Includes routers, switches, and firewalls. Although they don’t directly store data, these devices can be exploited to spread ransomware throughout the network.
- Database Servers: Databases that store critical information. Attacks on these servers can be very damaging if the data is encrypted by ransomware.
- Cloud Storage and Applications: Cloud-based services used to store and process data. Uncontrolled access or weak credentials can be a gateway for ransomware to enter.
In an organization’s Wide Area Network (WAN), ransomware can be a significant threat to data security. The main vulnerable points in this network include not only technological infrastructure but also human aspects such as users, administrators, and operators. In some cases of ransomware database hijacking, there are indications of involvement from people within the organization, both intentionally and unintentionally.
This understanding is expanded by comparing cloud storage management scenarios, whether managed by the organization itself or by a third party.
Visualization in the form of diagrams to better explain vulnerability points:
Human Vulnerability Points in WAN:
- Users: Often, users are the first and last line of defense against ransomware attacks. Those who are not vigilant can easily open malicious attachments or links that spread ransomware into the network.
- Network Administrators: They have extensive access to many parts of the network and its systems. Errors in security configurations or negligence in updating software can create opportunities for attackers to infiltrate.
- System Operators: Operators who manage the day-to-day operations of the network infrastructure are also important. Fatigue or lack of security training can lead to errors that allow ransomware to enter and spread.
Cloud Storage Management:
When comparing cloud storage management by third parties with internal management, there are several key security considerations:
- Security and Compliance: Third parties often have greater resources to invest in advanced security and meet strict compliance standards. This can reduce the risk of ransomware attacks compared to if the organization manages it itself without adequate resources, and Disaster Recovery Procedures that have passed various tests.
- Control and Accessibility: Managing cloud storage internally gives organizations more control over their data and its security. However, this also requires sufficient expertise from the internal team to secure data from ransomware threats.
- Incident Response: Third parties usually have well-tested and rapid incident response protocols, which are vital in minimizing damage from ransomware attacks. On the other hand, organizations that manage it themselves may take longer to identify and respond to such attacks.
In the context of WAN, the decision on whether to outsource cloud storage management or do it internally must consider these factors along with an evaluation of human security. Success in facing the ransomware threat heavily relies on the ability to integrate technological solutions with security awareness and effective operational protocols.
Review Conclusion:
Integrating an understanding of human vulnerabilities with strategic decisions about cloud storage management can significantly improve the WAN security posture against ransomware. Organizations must continuously assess and adjust their security approaches to effectively protect their digital assets against evolving ransomware and other cyber threats.